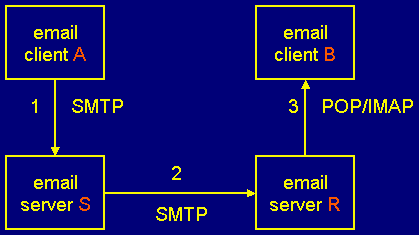
Name Resolution
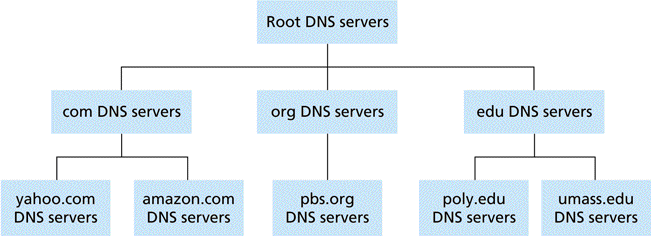
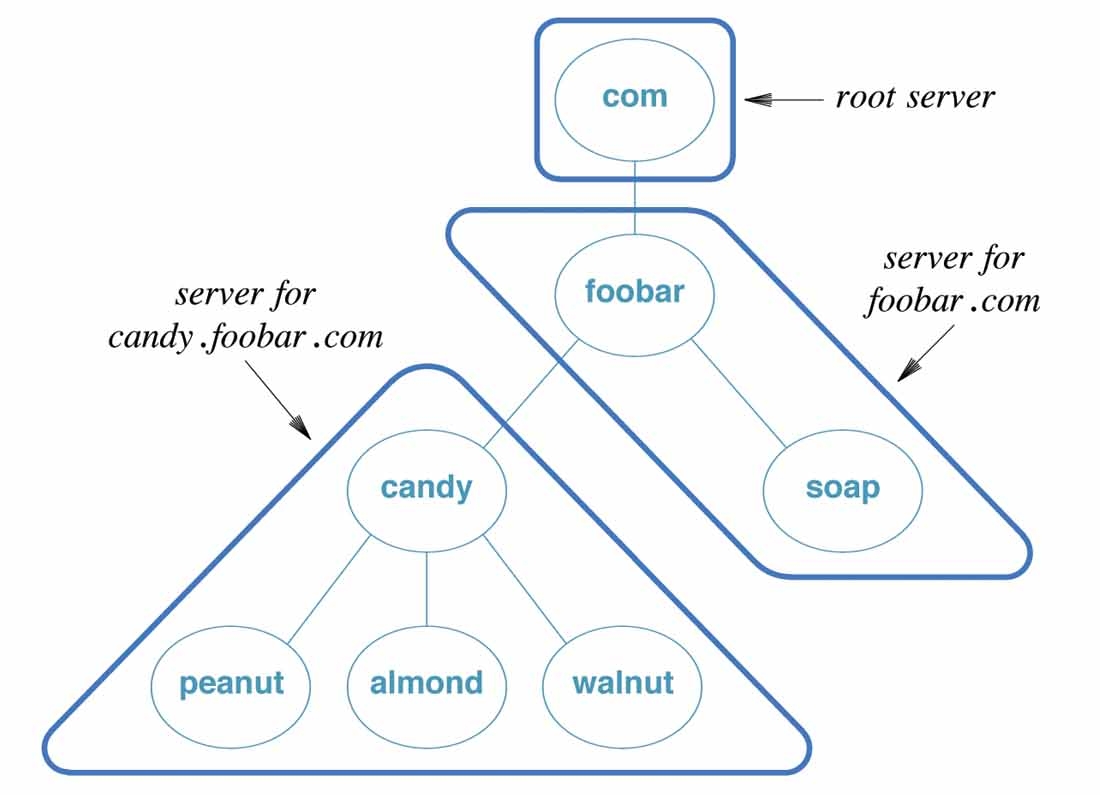
- translation of a domain name into an address is called name resolution
- the name is said to be resolved to an address
- software to perform the translation is known as a name resolver (or simply resolver)
- this software is usually built in to the application
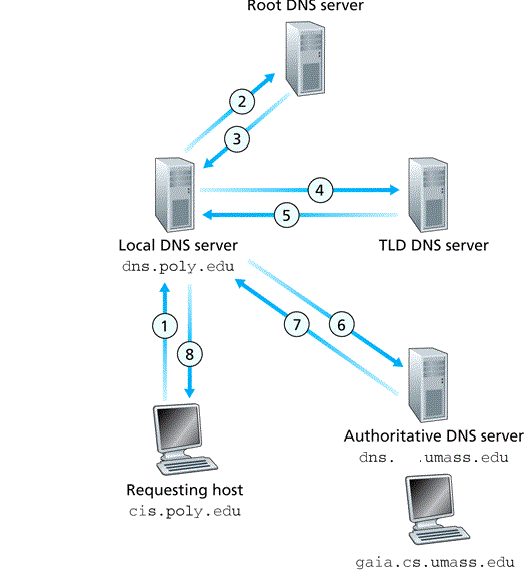
- a resolver uses the DNS protocol to contact a DNS server on port 53
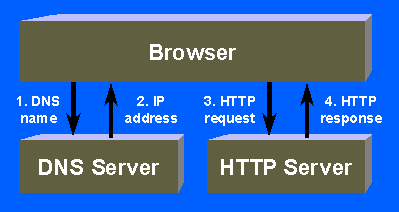
- e.g., browser uses a DNS server to map DNS name to IP address as follows: